Vulnerabilities in Microsoft Exchange Server
Posted by Joe Vigorito on Mar 11, 2021 10:00:00 AM
Current Status of Hafnium
Coming on the heels of the still evolving SolarWinds data breach, it is now verified that four previously unknown or "zero-day" vulnerabilities in Microsoft Exchange Server are being used in widespread attacks against thousands of organizations, with many more potentially affected, according to security researchers.
Microsoft on Friday, March 5, warned of active attacks exploiting unpatched Exchange Servers carried out by multiple threat actors, as the hacking campaign is believed to have infected tens of thousands of businesses and government entities in the U.S., Asia, and Europe.
The company said, "it continues to see increased use of these vulnerabilities in attacks targeting unpatched systems by multiple malicious actors beyond HAFNIUM," signaling an escalation that the breaches are no longer "limited and targeted," as was previously deemed.
These bugs are being tracked as CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. Microsoft, which issued emergency patches for last week, attributed the attacks to a newly discovered hacking team it calls Hafnium, identified as most likely a China-backed group. Microsoft said they were "limited targeted attacks" but warned they could be more widely exploited in the near future.
While an extremely fluid situation, the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) has issued an order to agencies to apply the patches for on-premise Exchange systems or to simply disconnect vulnerable servers after seeing "active exploitation" of the vulnerabilities. In other words, patch immediately or risk losing this critical infrastructure element in your enterprise. Microsoft further cautioned Exchange customers, "nation-state actors and criminal groups will move quickly to take advantage of any unpatched systems."
CISA over the weekend warned that it was "aware of widespread domestic and international exploitation" of Microsoft Exchange Server vulnerabilities and urged the scanning of Exchange Server logs with Microsoft's IOC detection tool to help determine compromise.
According to independent cybersecurity journalist Brian Krebs, at least 30,000 entities across the U.S. — mainly small businesses, towns, cities, and local governments — have been compromised by an "unusually aggressive" Chinese group that has set its sights on stealing emails from victim organizations by exploiting previously undisclosed flaws in Exchange Server.
Victims are also being reported from outside the U.S., with email systems belonging to businesses in Norway and the Czech Republic impacted in a series of hacking incidents abusing the vulnerabilities. The Norwegian National Security Authority said it has implemented a vulnerability scan of IP addresses in the country to identify vulnerable Exchange servers and "continuously notify these companies."
History suggests many organizations do not update their software when vulnerabilities are found. Microsoft last year warned Exchange server customers to patch the critical flaw CVE-2020-0688 but found that months afterwards tens of thousands of Exchange servers remained unpatched, despite nation-state attackers exploiting the bug from the outset.
History of Hafnium Attack
Beginning in January 2021, Mandiant (part of FireEye) Managed Defense observed multiple instances of abuse of Microsoft Exchange Server within at least one client environment. The observed activity included creation of web shells for persistent access, remote code execution, and reconnaissance for endpoint security solutions. Our investigation revealed that the files created on the Exchange servers were owned by the user NT AUTHORITY\SYSTEM, a privileged local account on the Windows operating system. Furthermore, the process that created the web shell was UMWorkerProcess.exe, the process responsible for Exchange Server’s Unified Messaging Service. In subsequent investigations, we observed malicious files created by w3wp.exe, the process responsible for the Exchange Server web front-end.
In response to this activity, they built threat hunting campaigns designed to identify additional Exchange Server abuse. Mandiant also utilized this data to build higher-fidelity detections of web server process chains. On March 2, 2021, Microsoft released a blog post that detailed multiple zero-day vulnerabilities used to attack on-premises versions of Microsoft Exchange Server. That post is detailed here.
There are two updates to this post that are of considerable importance:
Update 1 - 3/9/2021: Microsoft continues to see increased use of these vulnerabilities in attacks targeting unpatched systems by multiple malicious actors beyond HAFNIUM. To aid customers in investigating these attacks, we are sharing the following resources:
- MSRC has provided additional resources, including new mitigation guidance: Microsoft Exchange Server Vulnerabilities Mitigations – March 2021
Update 2 - 3/8/2021: The Exchange Server team released a script for checking HAFNIUM indicators of compromise (IOCs). See Scan Exchange log files for indicators of compromise.
Path Forward and Risk of Exploitation
The colossal scale of the ongoing offensive against Microsoft's email servers usurps the SolarWinds hacking spree that came to light last December, which is said to have targeted as many as 18,000 customers of the IT management tools provider. The SolarWinds attack seems to have only gone after high-value targets based on an initial reconnaissance of the victim machines.
A successful exploitation of the flaws in the Microsoft Exchange attack allows adversaries to break into Microsoft Exchange Servers in target environments and subsequently allow the installation of unauthorized web-based backdoors to facilitate long-term access. With multiple threat actors leveraging these zero-day vulnerabilities, the post-exploitation activities are expected to differ from one group to the other based on their motives.
Critical Considerations
The four security issues in question were patched by Microsoft as part of an emergency out-of-band security update last Tuesday, The U.S. Cybersecurity and Infrastructure Security Agency (CISA), which released an emergency directive warning of "active exploitation" of the vulnerabilities, urged government agencies running vulnerable versions of Exchange Server to either update the software or disconnect the products from their networks.
Doing nothing more but installing the patches issued by Microsoft would have no effect on servers that have already been leveraged and backdoored. For organizations where the web shell and other post-exploitation tools continue to remain deployed already at risk of future compromise until the artifacts are completely rooted out from their networks.
Cybersecurity firm Volexity, one of the firms credited with discovering the flaws, said the intrusion campaigns appeared to have started around January 6, 2021.
The origin of the attackers remains unknown, but Microsoft has primarily attributed the exploits with high confidence to a group it calls Hafnium, a skilled government-backed group operating out of China. Mandiant is tracking the intrusion activity in three clusters, UNC2639, UNC2640, and UNC2643, adding it expects the number to increase as more attacks are detected.
Determining Victimization
As referenced above under Critical Considerations, and while not exhaustive, the IOCs in this link are a strong initial step in determining your exposure and if you have already been exploited by this attack.
Moreover, as indicated in the CISA alert, follow these steps:
Conduct Forensic Analysis and Contact or Secure Your Incident Response Provider
Should your organization see evidence of compromise, your incident response should begin with conducting forensic analysis to collect artifacts and perform triage. Please see the following list of recommendations on how to conduct forensic analysis using various tools.
While collecting artifacts to perform triage, use processes and tools that minimize the alteration of the data being collected and that minimize impact to the operating system itself.
Ideally, during data collection, store the data on removable/external media and, when possible, run the artifact collection tools from the same media.
Key artifacts for triage that should be collected:
- Memory
- All registry hives
- All windows event logs
- All web logs
Memory can be collected with a variety of open source tools (e.g., FTK Imager by AccessData, Ram Capture by Belkasoft).
Registry and Windows Event logs can be collected with a variety of open source tools, as well (e.g., FTK_Imager, Kroll Artifact Parser And Extractor [KAPE]).
Web logs can also be collected with a variety of open source tools (e.g., FTK Imager).
Windows Artifact Collection Guide
Execute the following steps in order.
1) Download the latest FTK Imager from https://accessdata.com/product-download/
Note: Ensure your review of and compliance with the applicable license associated with the product referenced, which can be found in the product’s User Guide. The United States Government does not endorse any commercial product or service, including any subjects of analysis. Any reference to specific commercial products, processes, or services by service mark, trademark, manufacturer, or otherwise, does not constitute or imply their endorsement, recommendation, or favoring by the United States Government.
2) Collect memory from live system using FTK Imager. See Memory Capture with FTK Imager.pdf for instructions. Note: Download and copy “FTK Imager” folder to an external drive. Run FTK Imager.exe from the FTK Imager folder from external drive. Wait until memory collect is complete before proceeding to step 2.
3) Collect important system artifacts using KAPE. See KAPE Collection Procedure. Note: Download KAPE from a separate system; do not download KAPE to the target system. Run KAPE from external drive.
4) Collect disk image using FTK Imager. See Live Image with FTK Imager.pdf for instructions. Note: Run FTK Imager.exe from the “FTK Imager” folder from external drive.
Memory Capture with FTK Imager
1) Open FTK Imager. Log into the system with Administrator privileges and launch “FTK Imager.”
2) Open “Capture Memory." Select “Capture Memory…” from the File menu.
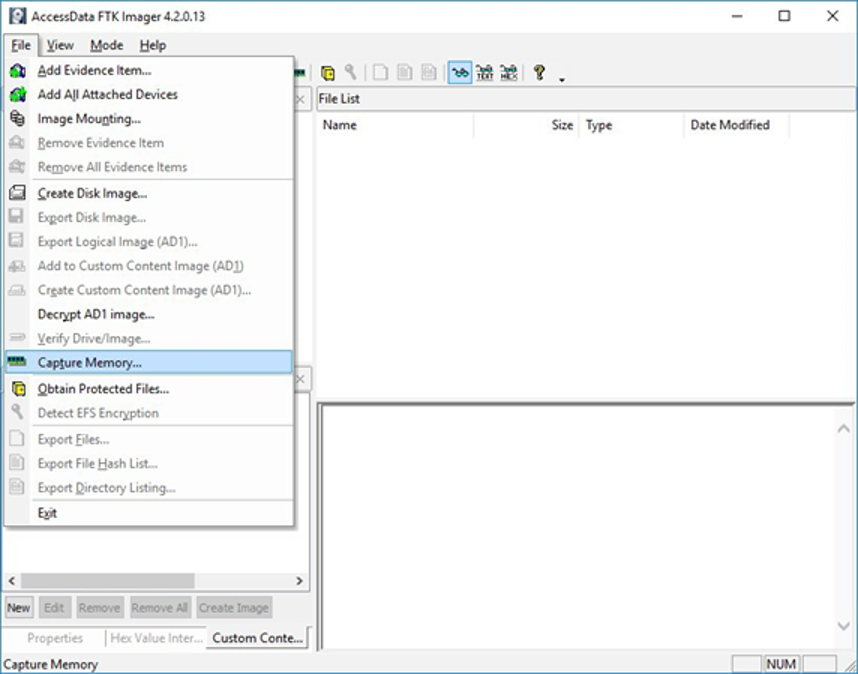
Figure 1: FTK Imager – Capture Memory Command
3) Select Path and Filenames. On the window that appears, use the “Browse” button to identify the destination of the memory capture. Save the memory capture to an external device and not the main hard drive of the system. Doing so will prevent the saved file from overwriting any dataspace on the system.
Name the destination file with a descriptive name (i.e., hostname of the system).
Select the box “Include pagefile” and provide a name of the pagefile that is descriptive of the system.
Do not select “Create AD1 file.”
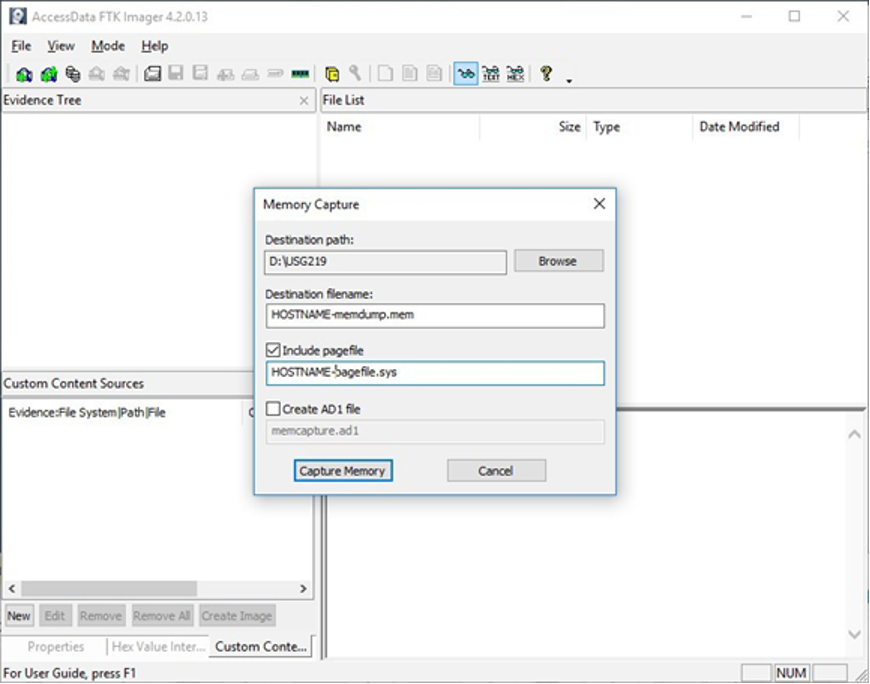
Figure 2: FTK Imager – Memory Capture
4) Capture Memory. Click on “Capture Memory” to begin the capture process. The process will take several minutes depending on the size of the pagefile and the amount of memory on the system.
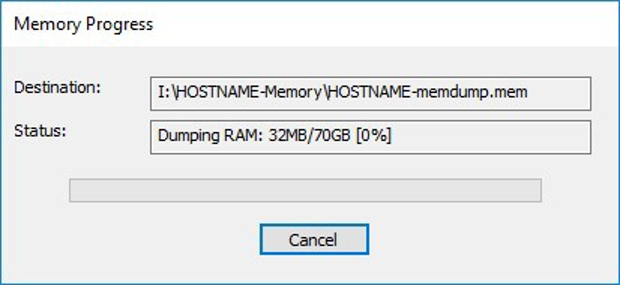
Figure 3: FTK Imager – Capture Process
KAPE Collection Procedure [1]
1) Download KAPE (read more about KAPE Enterprises first here) from https://www.kroll.com/en/services/cyber-risk/investigate-and-respond/kroll-artifact-parser-extractor-kape
2) Disable any antivirus or host protection mechanisms that prevent execution from removable media, or data loss prevention (DLP) mechanisms that restrict utilization of removable media.
Enable antivirus and host protection once this process is completed.
3) Unzip Kape.zip and run gkape.exe as admin from your removable media
4) Target source should be the drive on which the OS resides, typically C:.
5) Target destination should be an external drive folder, not the same drive as the Target source. If available, use an external hard drive or flash drive.
A KAPE execution with these parameters will typically produce output artifacts with a total size of 1-25 GB.
If you are going to be running KAPE on different machines and want to save to the same drive, ensure the Target destination folder is unique for each execution of KAPE.
6) Uncheck Flush checkbox (it is checked natively).
7) Check Add %d and Add %m checkboxes.
8) Select ALL checkboxes to ensure KAPE will target all available data that it is capable of targeting. This takes some time; use the down arrow and space bar to move through the list quickly.
9) Check Process VSCs checkbox.
10) Select Zip radio button and add Base name TargetOutput.
11) Ensure Deduplicate checkbox is checked (it is checked natively).
At the bottom you should now see a large Current command line, similar to:
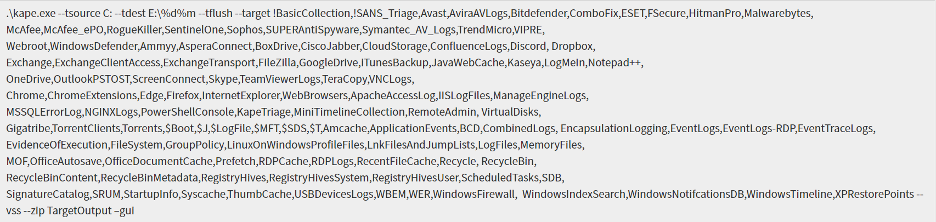
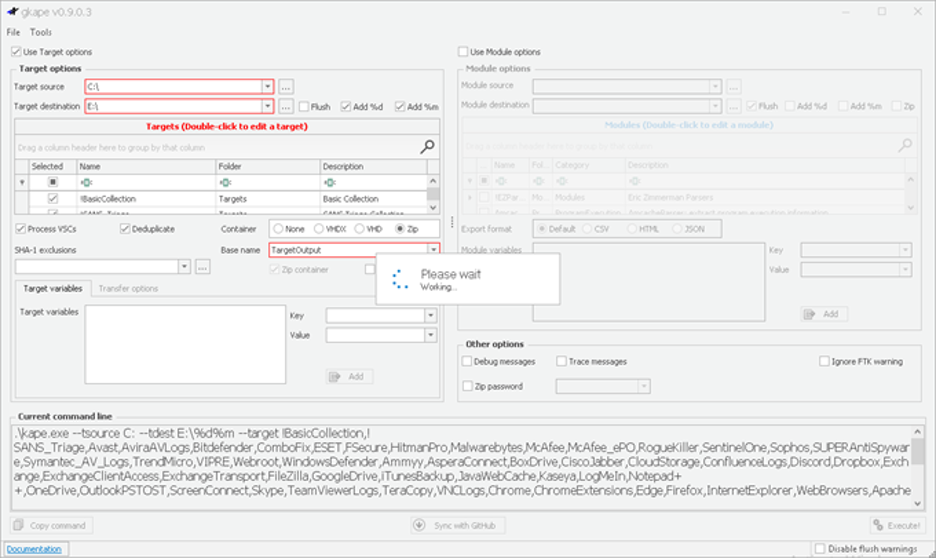
Figure 4: gkape.exe screenshot
Mitigations
CISA strongly recommends organizations read Microsoft’s advisory and security blog post for more information on how to look for Hafnium and to apply critical patches as soon as possible.
(Updated March 4, 2021): CISA is aware of threat actors using open source tools to search for vulnerable Microsoft Exchange Servers. This particular type of attack is scriptable, allowing attackers to easily exploit vulnerabilities through automated mechanisms. CISA advises all entities to patch as soon as possible to avoid being compromised.
Note, As per the 3/4/2021 update: From Microsoft's patch release, the security updates are available for the following operating systems:
Exchange Server 2010 (update requires SP 3 or any SP 3 RU – this is a Defense in Depth update)
Exchange Server 2013 (update requires CU 23)
Exchange Server 2016 (update requires CU 19 or CU 18)
Exchange Server 2019 (update requires CU 8 or CU 7)
(Updated March 4, 2021): If you are running an older CU then what the patch will accept, you must upgrade to at least the required CU as stated above then apply the patch.
All patches must be applied using administrator privileges and the recommendation from CISA is to disconnect vulnerable Exchange servers from the internet until a patch can be applied.
Note, As per the 3/5/2021 update: If patching is not an immediate option, CISA strongly recommends following alternative mitigations found in Microsoft’s blog on Exchange Server Vulnerabilities Mitigations. However, these options should only be used as a temporary solution, not a replacement for patching. Additionally, there are other mitigation options available. CISA recommends limiting or blocking external access to internet-facing Exchange Servers via the following:
Restrict untrusted connections to port 443, or set up a VPN to separate the Exchange Server from external access; note that this will not prevent an adversary from exploiting the vulnerability if the attacker is already in your network.
Block external access to on-premise Exchange:
Restrict external access to OWA URL: /owa/.
Restrict external access to Exchange Admin Center (EAC) aka Exchange Control Panel (ECP) URL: /ecp/.
Take Action
If affected, please contact your ConvergeOne National Account Manager for taking Incident Response action, if you have not already done so.
If you do not have a ConvergeOne National Account Manager, contact Joe Vigorito or Chris Ripkey.
Patch affected systems as rapidly as possible using emergency patching procedures. If you do not have such procedures, please contact us as noted above. Note, patching is the only complete mitigation and has no impact to functionality but will not evict an adversary who has already compromised your server. This blog post, updated on 3/10/21, has details on how to install the security update and other important information regarding Hafnium.
Links to Further Resources
Topics: Security, Cyber Security, Cyber Awareness

